About Us
Our company is a professional provider of web3 cybersecurity services. We believe that the decentralized nature of the web3 ecosystem requires a new approach to security, and we are dedicated to protecting our clients from threats that traditional cybersecurity measures might miss.

Introduce
We Commited to Develope Your Brand
Id consectetur purus ut faucibus pulvinar elementum. At elementum eu facilisis sed odio morbi quis. Vitae auctor eu augue ut lectus arcu. Erat pellentesque adipiscing commodo elit at imperdiet dui. Tellus mauris a diam maecenas. Odio aenean sed adipiscing diam donec adipiscing tristique.
Vision & Mission

Our Vision
Our Mission
Our team is made up of experts in the field of web3 technology and cybersecurity. We have a deep understanding of the unique security challenges faced by web3 applications and are constantly innovating to stay ahead of emerging threats.
In addition to our technical expertise, we are also committed to providing exceptional customer service. We work closely with our clients to understand their specific needs and design customized security solutions to fit their individual requirements.
We are proud to have a track record of successfully safeguarding the assets of some of the world’s leading web3 companies. If you are looking to secure your web3 application or platform, we would be happy to discuss how we can help.
Take advantage of your 1 Month free trial.
Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum.
Article, News & Post
Recent Blog & Post
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Mi ipsum faucibus vitae aliquet nec.
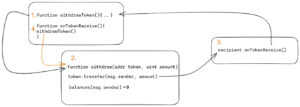
A guide to reentrancy: abusing the external calls for fun and profit
The reentrancy vulnerability is one of most serious ones that can be found in solidity smart contracts. Apart from the “classic” reentrancy like the one
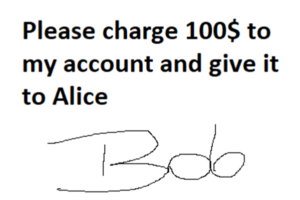
Ethereum signatures for hackers and auditors 101
In real world you can sign documents using your personal signature, which is assumed to be unique and proves that you support, acknowledge or commit
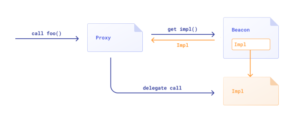
Common proxy vulnerabilities in Solidity part 1
Proxies are used to implement upgradeability in Solidity smart

Automated auditing part 1 – fuzzing with Echidna
What is Echidna? In this part, we will cover

