Blog
We want to work to increase knowledge and awareness in the field of web3 security.
We regularly publish articles describing niche topics, issues and solutions.
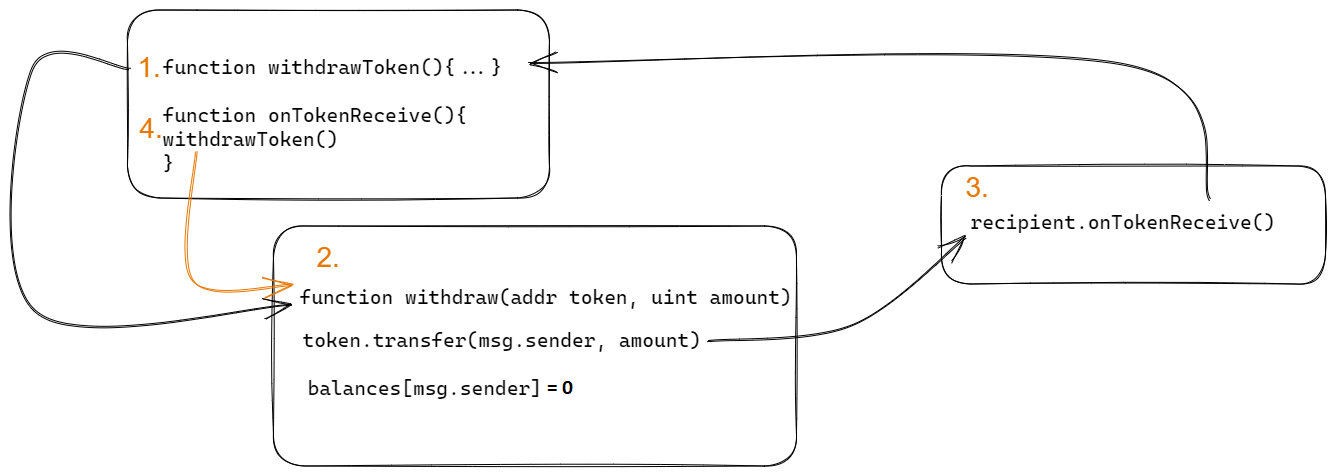
A guide to reentrancy: abusing the external calls for fun and profit
The reentrancy vulnerability is one of most serious ones that can be found in solidity smart contracts. Apart from the “classic” reentrancy like the one from the infamous DAO hack, there are other types of this vulnerability. In this article,
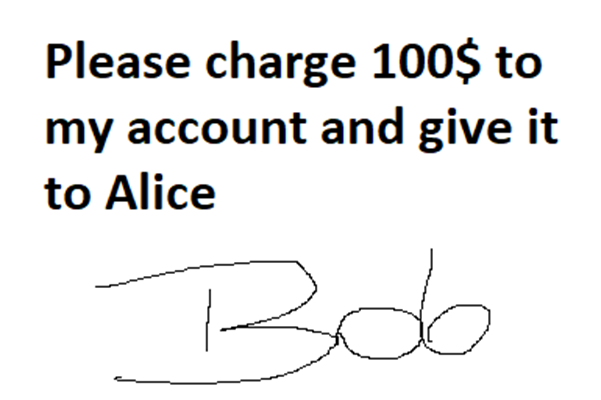
Ethereum signatures for hackers and auditors 101
In real world you can sign documents using your personal signature, which is assumed to be unique and proves that you support, acknowledge or commit something. The same can be done on ethereum blockchain and in solidity smart contracts –
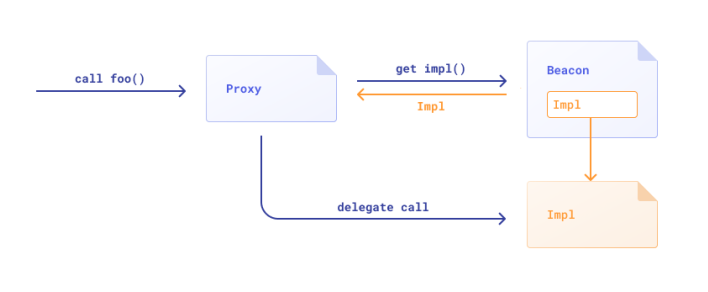
Common proxy vulnerabilities in Solidity – part 2
In the previous part, we explained some of typical proxy issues related to initialization, lack of state update or frontrunning. In this part, we would like to talk a bit about function and storage conflicts and also about decentralization. Proxy

Automated auditing part 2 – usage of AI for Smart Contracts testing
Introduction Creating a project or solution from scratch is a difficult and time-consuming process. A business concept must first be developed, then it must be translated into a high-level solution architecture, and finally the software development stage takes place. Because

Common proxy vulnerabilities in Solidity part 1
Proxies are used to implement upgradeability in Solidity smart contracts. They serve as a middleman between a contract and its users. They are employed to change a contract’s logic without altering its address. A master copy contract and a proxy

Automated auditing part 1 – fuzzing with Echidna
What is Echidna? In this part, we will cover the very basics of Echidna usage. Echidna is an animal, but it is also the name of a Solidity fuzzer. This tool is really worth mastering since a skilled user can

